When you remotely login to department computers, you must use a secure connection of some sort. Most UNIX and Mac OSX systems have a Secure Shell program (ssh) installed; solutions for Windows systems are also available. A Secure Shell program is the functional equivalent of telnet or rlogin, but with several advanced features. Most importantly, it provides an encrypted connection between the two machines, making eavesdropping and session hijacking impossible. It also provides X display forwarding, provided you have an X-server running on your local machine. Likewise, it can also provide arbitrary port tunneling between machines, providing a secure connection for any service.
Secure Shells programs also provide secure file-transfer capability, via the sftp (Secure FTP) or scp (Secure Copy) commands. These are secure replacements for the insecure services ftp and rcp.
Setting up SSH key authentication
1. Download and install MobaXterm
https://mobaxterm.mobatek.net/
2. Genearate a Public/Private Key Pair
- Run the MobaXterm SSH Key Generator. Tools --> MobaKeyGen (SSH Key Generator).
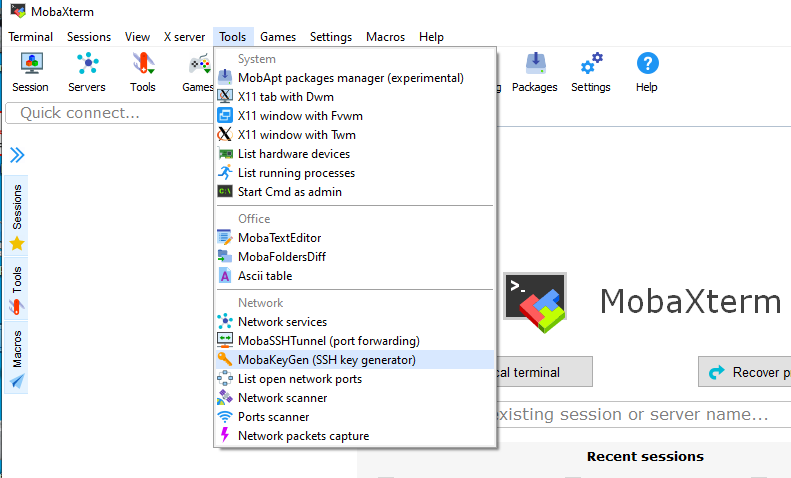
- Set the 'Type of key to generate' to 'ed25519'.
- Select 'Generate'.
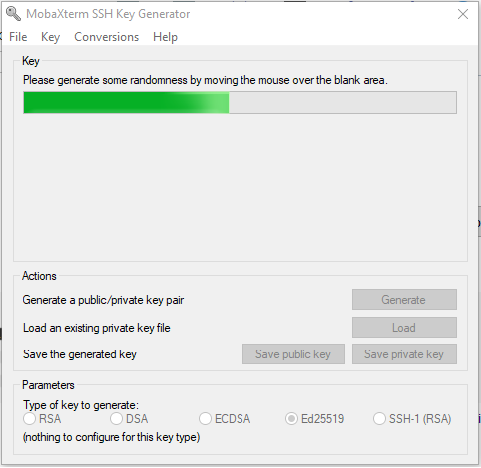
- Optional Step: If you want to add a passphrase to your key, do that now. A passphrase will prevent unauthorized use of your key without the passphrase, but you will need to enter this passphrase every time you use your SSH key. To add a passphrase, enter your passpharse in the 'Key passphrase' and 'Confirm passphrase' text boxes.
- Save your private and public key. To save the private key, select 'Conversions --> Export OpenSSH key'. Save the public key with the 'Save public key' button. Remember to keep your keys in a secure location.
- Now copy the contents of the text box titled "Public key for pasting into OpenSSH server". It is the yellow-highlighted text in the image below. This is the public key string you will need in the next step.
3. Install the public key
- SSH into login.cs.duke.edu using your NetID username and password.
- Open the .ssh/authorized_keys file in your home directory with your favorite editor (nano, pico, vi or vile):

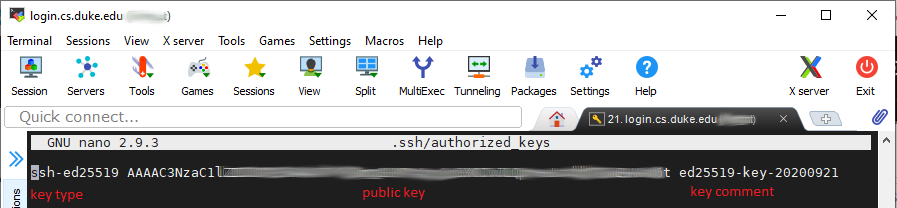
- Paste in the your public key string and save the file. The key entry should look like the following image. It starts with 'ssh-ed25519' followed a space and your key:
4. Create a MobaXterm session that uses your keys
- Inside MobaXterm, click on the Session button and select 'SSH'.
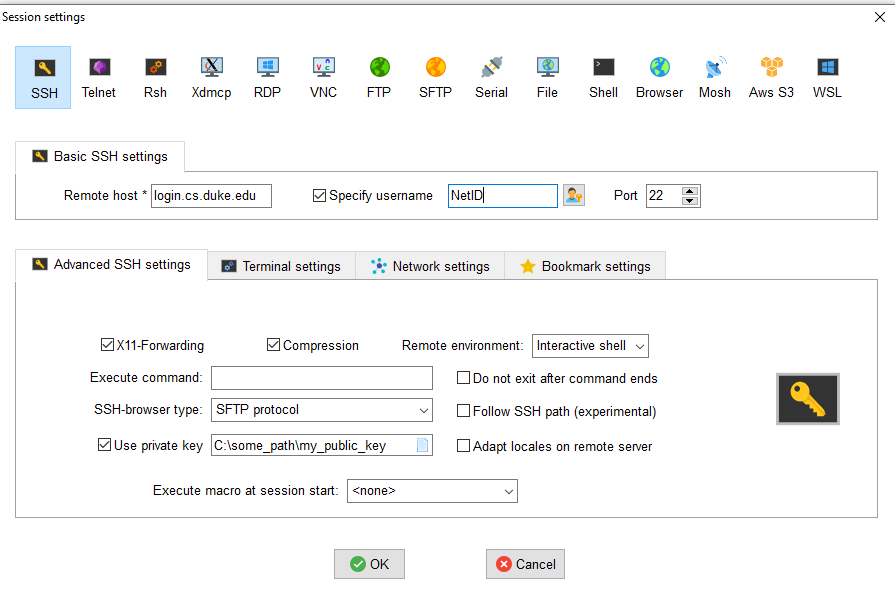
- Under the 'Basic SSH settings' section, enter the Remote Host name - this is the server that you installed your public key to earlier. In this example, it would be login.cs.duke.edu.
- Click the 'Specify username' checkbox and enter your NetID username.
- On the 'Advanced SSH Settings' tab, Click the 'Use private key' checkbox and enter the path of your saved private key.
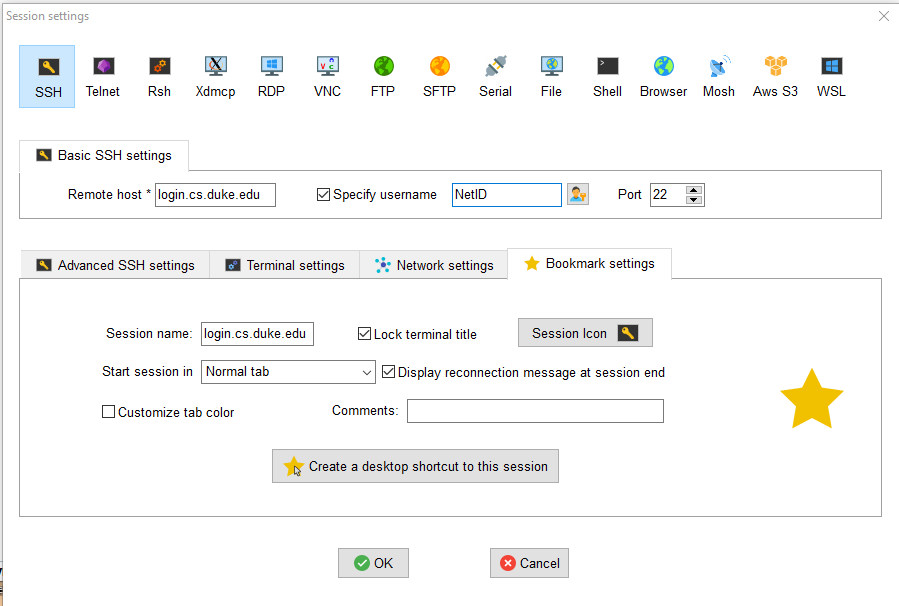
- Now click on the 'Bookmark settings' tab and save this session for future use. Provide a 'Session Name' that you'd like and hit OK.
Find and open the Terminal. You can find the Terminal app by going to Applications > Utilities > Terminal.
Once you have the Terminal open, use the following command to generate a key-pair:
ssh-keygen -a 100 -t ed25519 -f ~/.ssh/id_ed25519
The command will prompt you to enter a passphrase for the key-pair. It is recommended you enter a passphrase but it is not required. If you do not wish to enter a passphrase, you can hit enter twice. You will then be given a key fingerprint and a random art image. The key files should now be generated in your home directory under the .ssh directory. The key filenames will be id_ed25519 and id_ed25519.pub. If you have already generated a key from another process, a warning may appear telling you that the key already exists and would you like to overwrite. Type n to exit without overwriting and select a new name for your keys by changing the id_ed25519 filename in the previous command above.
Once you have you keys generated, the public key must now be copied to the host you wish to log in to. The easiest way to do that is by issuing the following command:
ssh-copy-id -i ~/.ssh/id_ed25519.pub <your netid>@login.cs.duke.edu
You will be prompted for your password to login.cs.duke.edu. Make sure to use your netid password and not your CS password. The command will make sure your key is set up correctly. Once the command is run correctly, you should be able to ssh into login.cs.duke.edu without entering your password. These steps are the bare minimum you need to enable ssh key authorization to login.cs.duke.edu. If you decided to add a passphrase to your key and are running Mac OSX Sierra 10.12.2 or later, you can configure your SSH to automatically load your keys and store your passphrase in Keychain. First you must edit the ssh configuration file:
~/.ssh/config
and add the following section:
Host * AddKeysToAgent yes UseKeychain yes IdentityFile ~/.ssh/id_ed25519
Once the configuration has been updated you can add your key to the SSH agent with the following command:
ssh-add -K ~/.ssh/id_ed25519
The SSH protocol allows the use of multiple keys, so if you have more than you key, you can specify which key to use with the following command:
ssh -i ~/.ssh/id_ed25519 <netid>@login.cs.duke.edu
Or you can update your SSH config file with the following:
Host login
HostName login.cs.duke.edu
User <your netid>
IdentityFile ~/.ssh/id_ed25519
IdentitiesOnly yes
Once that configuration has been added, you should be able to issue the following command to log in to login.cs.duke.edu:
ssh login
MobaXterm has an SSH authentication agent that allows you to use your SSH keys many times without having to provide your passphrase each time. It also has an SSH forwarding option that allows SSH servers to connect directly to your MobaXterm SSH agent, even multiple connections away from your initial connection. To enable SSH Agent forwarding, in MobaXterm go to Settings --> Configuration --> SSH.

Check the 'Use internal SSH agent "MobAgent"' box. Then, under 'Load following keys at MobAgent startup', click on the '+' and browse to the location of your private key. You'll be prompted for your key passphrase each time you launch MobaXterm now. Press OK and you'll be prompted to restart MobaXterm to enable MobAgent.
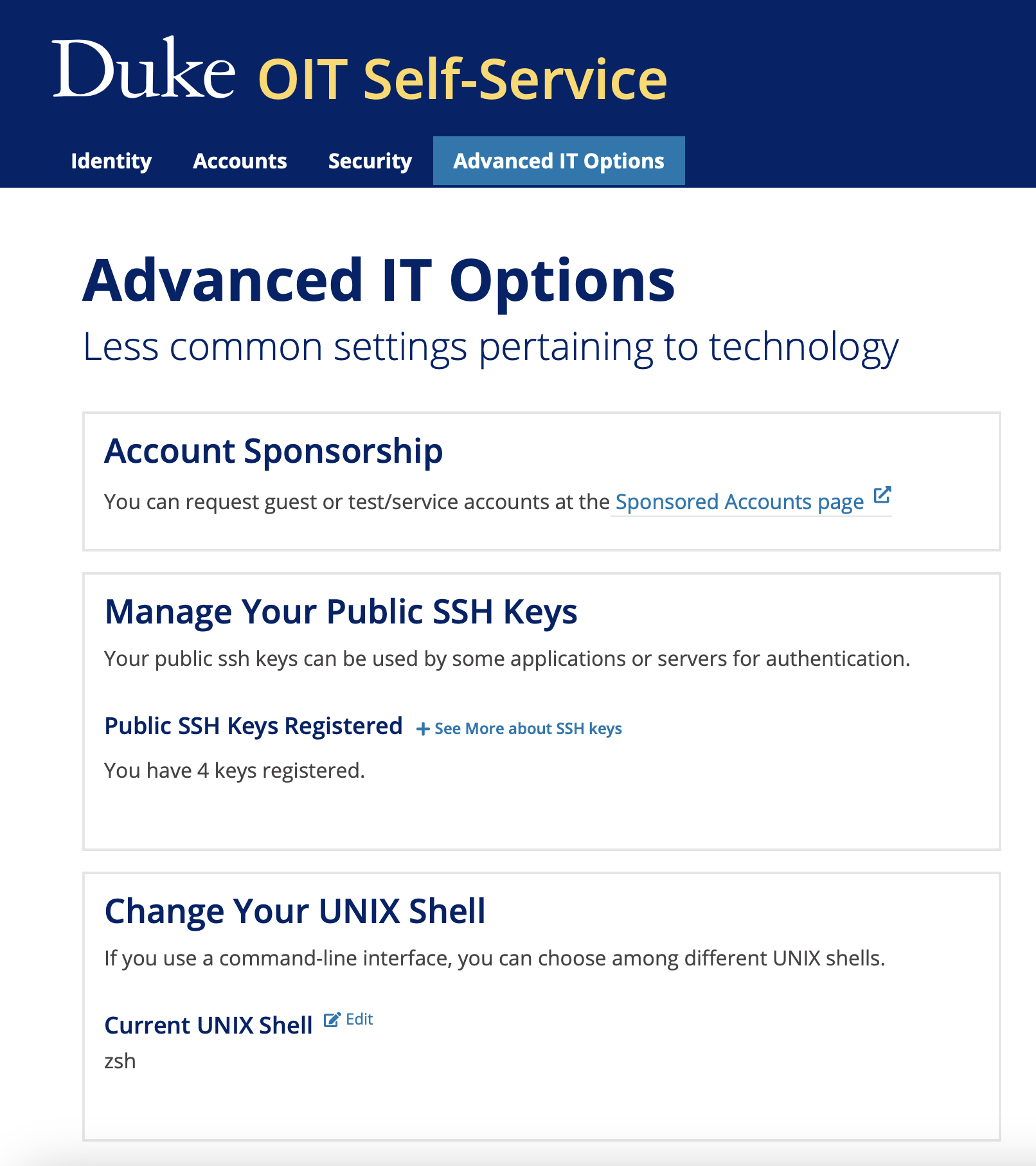
You can attach your public SSH key to your Duke account at the Account Self-Service portal. This will enable you to use your SSH keys to connect to Duke servers, as well the CS login server (login.cs.duke.edu).
To set this up, navigate to https://idms-web-selfservice.oit.duke.edu/advanced
Under the 'Manage Your Public SSH Keys', select the 'See More about SSH keys' and paste in your public key and 'Add Key'.